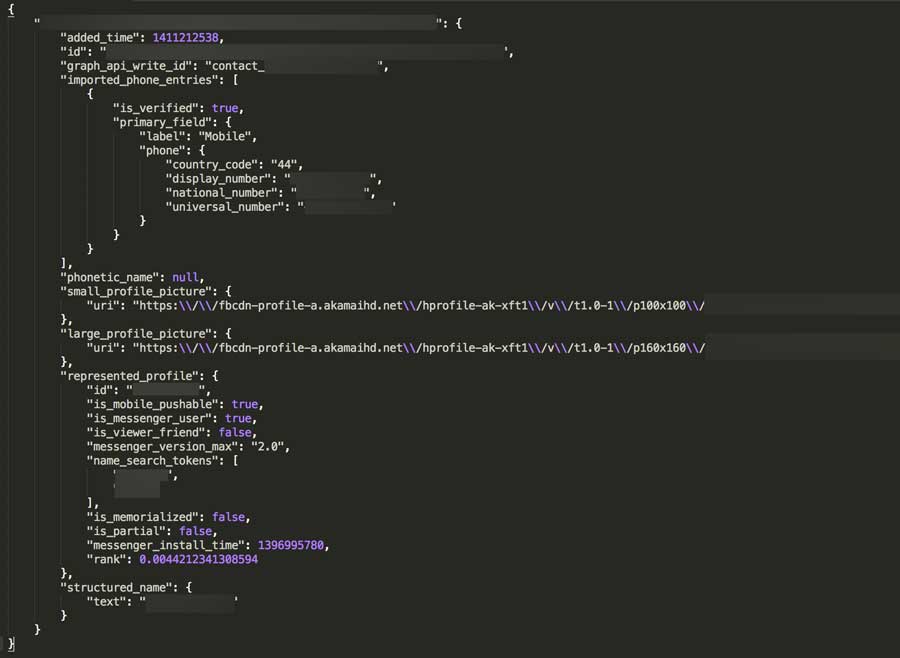
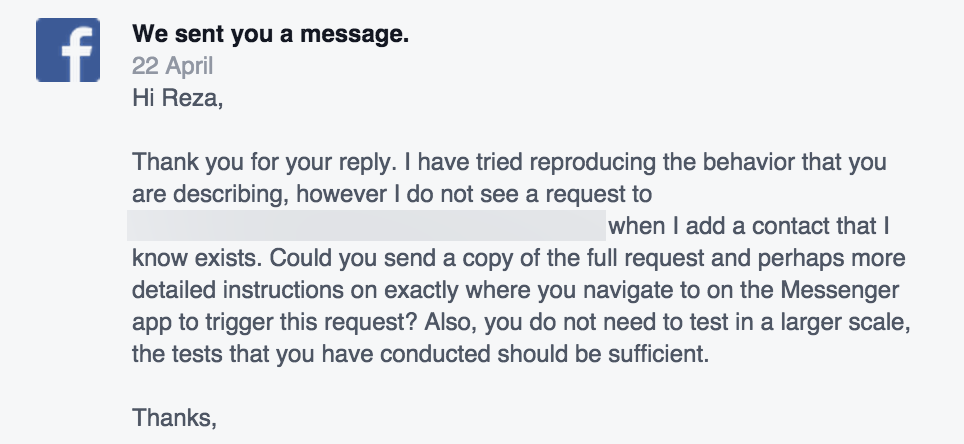
Reza Moaiandin, technical director of Leeds-based company Salt.agency discovered a way to harvest Facebook users data using just their telephone number. Writing on the company blog, he says he discovered the flaw by mistake. He used a simple method to harvest data using a little-known search feature which allows you to search for any Facebook user using only their phone number. Moaiandin says, Once he chanced upon the vulnerability in Facebook, he wrote an an algorithm that generated thousands of numbers automatically. Once he had generated these phone numbers, he sent these number through Facebook’s application programming interface (API). Once he had done that, Moaindin says that user profiles and personal data soon began pouring in. All of the data is publicly available, but as there is no limit to the number of searches an individual user can make, the loophole could be used to extract information about “millions” of users, according Moaiandin Moaiandin says that as soon as he discovered this vulnerability in the Facebook API, he alerted Facebook about the security flaw, however Facebook said that this was not a vulnerability.
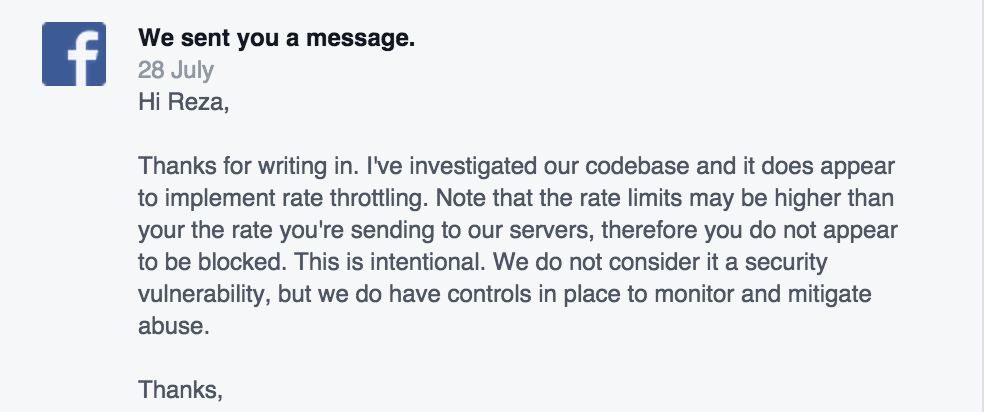
The Facebook spokesperson told him “We do not consider it a security vulnerability, but we do have controls in place to monitor and mitigate abuse.”
Moaiandin said that this flaw could be a huge phishing problem if no limit is created, and the loophole is discovered by the wrong person. The communication with those APIs needs to be pre-encrypted and/or other measures need to be taken before this loophole is discovered by someone who could do harm. The “Who can search for me?” setting is set to public by default, meaning that even if your mobile number is withheld on the site, it can still be used to find you using this loophole. We are reaching out to Facebook for comments on why this is not considered a vulnerability. If a limit is not placed on the implement rate, it could lead to data harvesting of thousands of Facebook users by cyber criminals.