2014 Protests in Hong Kong The 2014 Hong Kong protests, which is also known as the Umbrella Movement or Umbrella Revolution, began in September 2014 when activists in Hong Kong protested outside the government headquarters and occupied several major city intersections after the Standing Committee of the National People’s Congress (NPCSC) announced its decision to nominate only the Mainland China vetted candidates. The protesters who are made up of mostly students and pro-democracy advocacy groups based in Hong Kong dont want a Beijing controlled puppet government in Hong Kong and also want that they be allowed to nominate and choose their own leaders. The protests which started in September 2014 lost steam midway only to gather momentum again since 10th October. Pro Democracy websites Alliance for True Democracy (ATD), the Democratic Party Hong Kong (DPHK), People Power, and the Professional Commons are pro-democracy websites which were handling the vital logistics and communications between the protesters who are occupying the streets of Hong Kong. The Volexity researchers stated that of the above four, the websites of Alliance for True Democracy (ATD) and Democratic Party Hong Kong (DPHK) carry a potentially malicious JavaScript code is called from java-se.com domain, which Volexity believes to be associated with advanced persistent threat (APT). While examining the ATD website, Volexity also observed that the site had a password protected backdoor webshell placed on it. The purpose of the webshell is to maintain access to the compromised systems after the malicious code is detected and eliminated. Volexity refers to this shell as the Angel Webshell, named after its default password of “angel”. The shell will simply display the text “Password:”, a text input box, and a Login button. A screen shot of the webshell as observed on the ATD website can be seen below. Over the last two days, Volexity has observed malicious code being served up from the website of the Alliance for True Democracy (ATD) in Hong Kong (www.atd.hk). ATD is an alliance of people and organizations dedicated to democracy and universal suffrage in Hong Kong. At the time of this writing malicious code is still live on the website, so please visit with care until the website is clean. Below is a screen shot of the malicious code references found pre-pended to a JavaScript file on the website named superfish.js.
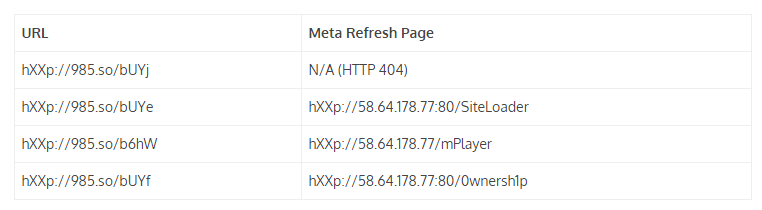
Peoples Power website contains malicious iframe as per Veloxity. The malicious iframes are pointing to exploit pages. The bad links have been shortened through the Chinese URL shortening service 985.so so as to evade detection. The researchers found four links of this sort, three of them directing to exploits hosted on a single IP address. “These pages load scripts that conduct profiling of the system for various software, plugins, and other related information, as well as load Java exploits designed to install malware on the target system. If successful, the exploits will install either a 32-bit or 64-bit version of the malware,” Adair says.
Volexity also discovered peculiar code on the website of a pro-democratic and pro-universal suffrage public policy think thank The Professional Commons (www.procommons.org.hk). In the case of this website, there is suspicious JavaScript code that writes an iFrame pointing back to a non-existent HTML page on a hotel website in South Korea. Users are warned that the above four sites still carry malicious code hence if you intend to visit them use sandboxing method.