Hackers are using the Google Drive to steal your login credentials and crucial data, suggests a new research.Modus Operandi of the Phishing campaign:Free Google Domain Phishing Campaign
On Monday, Security researchers have revealed that a new Gmail phishing campaign has been launched, most probably by a hacking team based in the Middle East. The team targets users of Gmail with fake SSL(Secure Sockets Layer) encryption which successfully tricks users into surrendering the login credentials of their Google accounts to these scammers. It is not yet clear as to how many users have been already attacked by these crooks. Just a year back Google Docs and Google Drive were the target of a sophisticated phishing scam and now the new campaign is similar to the last one with the only difference being this time the campaign is quite obfuscating. As per Aditya Sood, architect at Elastica Cloud Threat Labs, the obfuscation has been purposely designed to trick the victims. The major drawback here is Google does not have any in built safety mechanism for its Google drive and online document storage services nor does it scan the files for any malicious codes, if any. Phishing scammers are using this particular loophole to achieve success in their campaign.
Modus Operandi of the Phishing campaign:
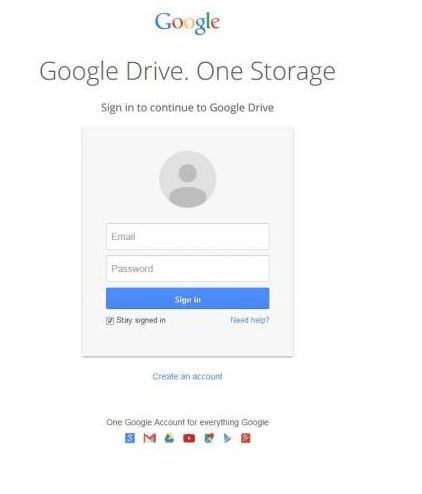
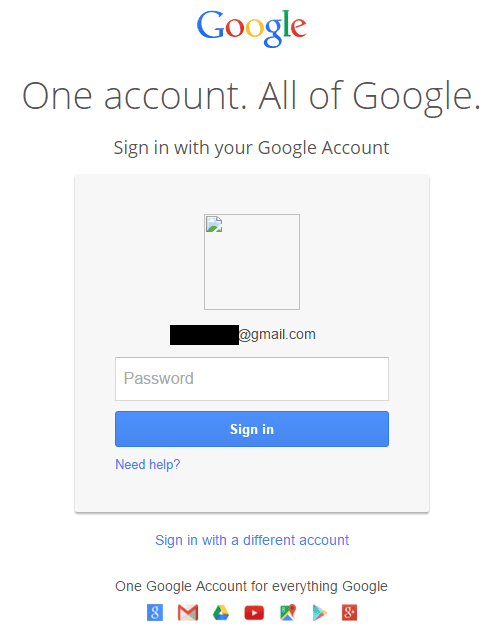
The Phishing campaign referred to by the researchers does not affect the user’s machine or device as they do not use any malware. Google Drive can be used for a variety of purposes, which includes storing documents, spreadsheets, presentations, photos and also to host an entire website. In this campaign the phishing scammers use the Google Drive to host a web page which mimics the Google account login screen and thus collect user’s login details. Sood says: “You can share this webpage externally with anyone.” The Google Drive Login page runs on javascript and phishing team has obfuscated it in such a way that it can collect the credentials and also deliver it to the attackers via some different website. As a matter of fact, all Google users routinely have to provide their login credentials such as their “username” and “password” whenever they log into their Google accounts. Why is this phishing campaign dangerous? Because here not only is the ‘fake login page’ hosted by Google but it also has been protected by Google’s SSL certificate. Hence, it is difficult for anyone to understand the difference between the real login page and the fake one. Sood says: “It uses the HTTPS that Google uses, and the Google Drive link, which is usually considered legitimate.” Further, the crooks distribute the links by using Google’s own mechanisms and hence the phishing emails resemble as if they are real business emails which is being shared by real people. The working of the phishing scam is so precise that neither the end users nor the Google’s spam filters can make out that it is a part of the phishing scam. In this case, once users provide their credentials, a PDF document gets loaded up due to which users cannot make out that they were phished. This PDF document contained a 2006 scientific paper from Christina K. Pikas, who is a doctoral student at the University of Maryland, and it is titled: “The Impact of Information and Communication Technologies on Informal Scholarly Scientific Communication: A Literature Review.” Google’s motto of single log in for all accounts further helps the phishing campaign, because generally there is only one single sign-in page where users can log and get access to multiple services. Hence, by attacking the log in page attackers get an easy access to user’s email, calendar, analytics, essential documents and any other service which victims have signed up for. Suppose, if the target of these phishing campaigners is an administrator of Google Apps that has been deployed for Business purpose then the scammers can get an easy access to the company’s major data including their communication emails and all other details. Sood added: “We reported this to Google through the standard security channel, and then followed up with their security team.” As per Sood, the phishing scam is still in progress however he feels it will not continue for long. “We’re are pretty sure that once Google gets on this particular thing, that they will remove it,” he said. “But, right now, it’s still active, so we’re letting people know so at least people won’t fall for it.” Ways to safeguard from being phished: In the meantime, Google users can be alert and watch out for certain signs which indicates that they are being attacked by the scammers. The real Google sign-in page states “One account. All of Google.” On the other hand the header of the fake page reads “Google Drive. One Storage.” In case of the fake page users will find a “Create an account” link which would just reload the same page and in case user types in the wrong password it would still work because attackers do not carry out the validation of the credentials.
So for now, all Google users if you get any link to documents on Google Drive from strangers do not click to open the link as it could be some phishing scam also while logging into your Google account be alert and check for all the details of a legitimate Google sign-in page before entering your credentials.
Free Google Domain Phishing Campaign
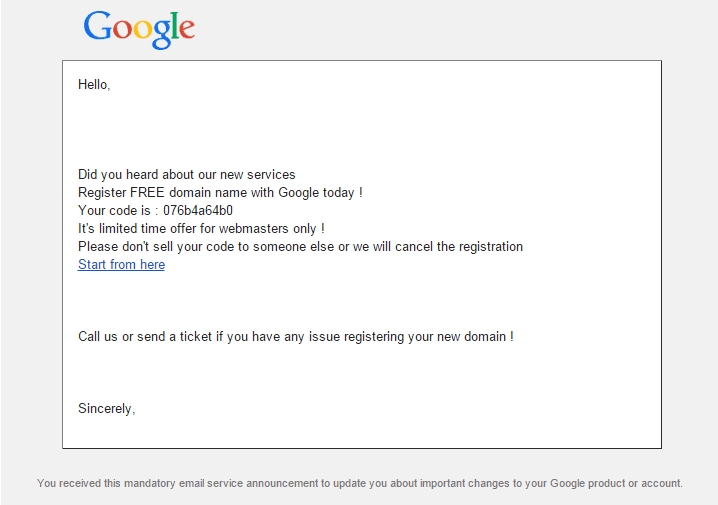
Another phishing campaign offers victims free Google Domain. The email which is sent to victims offers free domain registration.
The scammer have cloned a perfect Google logo and the terms and conditions at the bottom of the page. Clicking on the page takes the victim to a https://google-names.com/servicedo/076b4a64b0.php which is similar to the cloned Google Drive page above. It captures the email id of the sender but the only thing that the cloned page cant capture is the Google Avatar.
If you receive such kind of phishing emails be warned that giving out your details like handing keys to your entire Google account including your Android Smartphone, Google Drive, Google Photos and other Google products to the scammers.