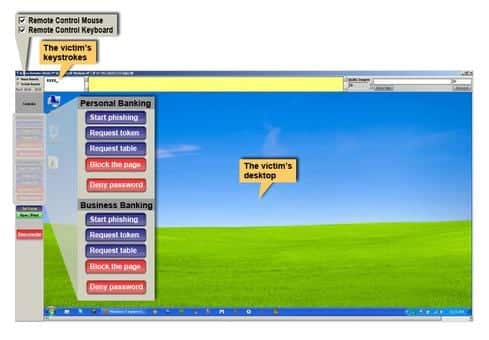
The added advantage for the criminals is that it effectively circumvents both two-factor authentication and device identification protections. IBM Security Trusteer who called it ‘virtual mugging’ tool, analysed it and has released a report detailing it. The report says that unlike banking Trojans, KL-Remote is less automated and requires some manual intervention from the criminal during various stages of the fraud event. KL-Remote is distributed by embedding it with other malware and comes preloaded with a list of targeted banking URLs. When the infected victim visits one of those sites, the malware operator gets an alert and can then decide whether or not to proceed with an attack.
As can be seen by the interface in the image above, it provides with a direct approach phishing buttons. To engage the victims, KL-Remote takes a snapshot of the original website the victim was viewing and presents it as an image on the screen of the infected computer. Once the victim is presented with this infected screen, the victim is dealing with the cyber criminal instead of the legitimate banking website.
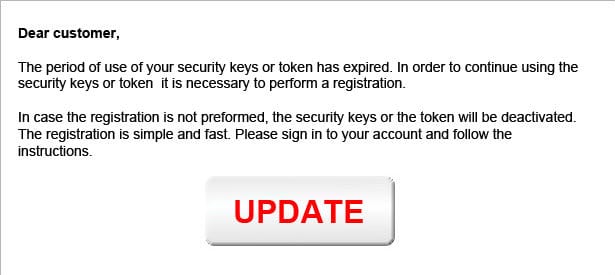
By pushing the “Start phishing” button, the criminal causes a message to appear on the victim’s screen. The tool contains separate messages for each of the targeted banks. Each message is customized to the bank’s website login/authentication process and copies its look and feel.
Believing it to be the original banking website if the victim clicks on the ‘update’ button he/she is presented with a new screen asking for the banking pin details:
Once the victim inputs the 6/4 digit pin number, he/she is locked out of the website and the cyber criminal is in total control of the victims banking website. The KL-Remote toolkit’s approach of directly performing the attack from the victim’s computer is able to bypass traditional protection methods. IBM Trusteer’s analysis has shown that the toolkit is able to circumvent or compromise the following security measures:
Username/Password: The toolkit lets the criminal present the victim with a pop-up requesting his or her username and password. Two-Factor Authentication: The toolkit lets the criminal present the victim with a pop-up asking for two-factor authentication (2FA), such as tokens or one-time passwords received out-of-band. Some types of 2FA require a physical element such as a USB authentication key. Since the attack is carried out from the victim’s computer while the victim is browsing the legitimate banking website, the victim is likely to have the USB key plugged in at the time of the attack. Device Identification: Due to the attack being conducted directly from the victim’s PC, any type of detection method based on the assumption that a known device is a safe device will be circumvented.
Though at present the KL-Remote is being used exclusively by cyber criminals based in Brazil and primarily targeting the Brazilian users with Portuguese language interface, IBM Security Trusteer analysis shows that it can be adapted to other languages, territories and industries. IBM recommends users and financial institutions take the following steps to protect themselves:
Avoid opening phishing emails. Never open attachments or click on links from suspicious emails or emails from unknown sources. Protect computers with dedicated financial malware endpoint protections such as IBM Trusteer Rapport. Deploy server-side protections that can detect evidence of malware infections and remote-controlled access of banking websites.