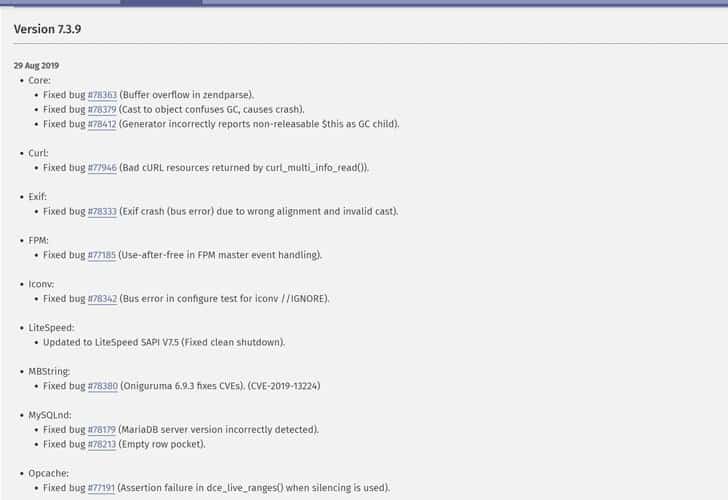
But now it is fixed with it’s latest patch release rolled out by PHP maintainers. The patch was released to fix multiple vulnerabilities which were resided in its core and bundled libraries. The most risky one could have allowed remote attackers to execute arbitrary code and compromise targeted servers. This is something very serious because PHP is a server-side web programming language that powers over 78 percent of the internet today. Depending on the type, occurrence, and usage of affected codebase in the PHP application, attackers were allowed to perform some serious damage using associated privileges. Even the failed attempts of exploitation could have resulted in DDoS ( Distributed Denial of Service) attacks. Talking about the patch, then it was very necessary as it could have left thousands of PHP powered web applications and websites at high risk. php Out of these, a ‘use-after-free’ code execution vulnerability, was assigned as CVE-2019-13224 which resides in Oniguruma. A popular regular expression library that comes bundled with PHP and many other popular programming languages. Any remote hacker or attacker can misuse this flaw by simply inserting a specially crafted regular expression in an affected web application and can cause information disclosure. But the Good news is there has no report of any such damage yet. So yes we can say that after updating to it’s latest patch you are safe.