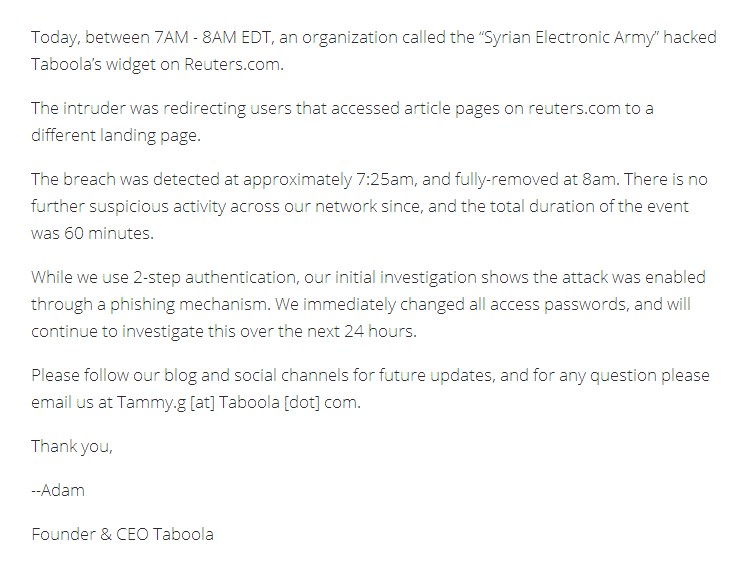
However experts says that it was not that the Reuters web servers which were breached in this hack. According to the sources, the Reuters website is managed by a third party ad provider Taboola and it is Taboola who is to be blamed. Many visitors who used adblockers on their browsers were not redirected, which meant that one of the code inserted from Taboola was poisoned by the Syrian Electronic Army. This makes it difficult to pin the blame on Taboola, because one of the admin’s account who managed the ads code on the website may also be responsible. Neither Taboola, nor Reuters have commented over the matter yet but a press release is soon expected. It is not the first time when Syrian Electronic Army has targeted a western media group, they keep doing it all the time as they believe that the Western world and media are pro rebels and against the Assad regime in Syria. Their official statement however always states that they do it when any media group makes any fake news about Syria or poke them about their ways. We have already contacted the Syrian Electronic Army for more information on the hack and will update you with one. UPDATE: Adam Singolda Founder & CEO of Taboola confirmed the breach in a blog post and said the attack was carried out using Phishing attack. The Company has changed all its access passwords and will continue to investigate the attack for next 24 hours, he said. Syrian Electronic Army too confirmed that the attack was carried out using Taboola. A tweet tweeted earlier today shows the screenshot taken by the SEA from Taboola’s Paypal account.